SIEM consulting near you
Get more visibility and transparency with a security management system
A Security Information and Event Management (SIEM) system collects data from various data sources within the network infrastructure, servers, systems, devices and applications, from the traditional perimeter to the end user.
A deployed SIEM solution thus provides a centralized view of all insights about your users, key assets and their context. Data is consolidated and analyzed for timely detection of deviations or potential threats.
Possible data sources include:
-
Network devices: routers, switches, bridges, wireless access points, modems, line drivers, hubs.
-
Servers: Web, proxy, mail, FTP
-
Security devices: IDP/IPS, firewalls, antivirus software, content filtering device, intrusion detection applications
-
Applications: Any software used on any of the above devices.
What is a SIEM solution?
Why are SIEM solutions needed at all?
With a deployed SIEM solution, you get detailed insights into data analysis. All collected data is collected in a central location. The SIEM software analyzes all data and categorizes it accordingly. As a result, a context is provided that gives insight into the internal security events within the infrastructure.
When choosing a SIEM solution, it is important to define the scope beforehand. Starting from simple log management and change functionalities up to meaningful dashboards.
Take advantage of meaningful SIEM dashboards such as:
-
Overview of relevant events in your environment that could potentially cause security incidents.
-
Details on all relevant events identified in your environment so you can sift through and prioritize them
-
Risk analysis for risk ranking of systems and users in your network to identify risks
-
Web information for analyzing web traffic on your network
Request SIEM Audit
Get deep insights into your IT infrastructure.
Identify and analyze all the data already in use in your organization and assess it with a view to security risks, data usage and legal compliance. Get concrete recommendations for action for your organization so you can get started with implementation right away. For more security of your data and its use in the cloud.
We will be happy to send you personal appointment proposals for the CYQUEO SIEM Audit virtual session.
Request your SIEM Audit now
These advantages you get by using SIEM
Advantages of using SIEM
There are numerous benefits that come from using Security Information and Event Management. These benefits include:
- fast and reliable detection of threats
- Fast and appropriate response to security-related events
- adherence to legal requirements and compliance regulations
- Savings in IT security personnel through automation
- retrospective proof of security events
- tamper-proof and audit-proof storage of all security-relevant events
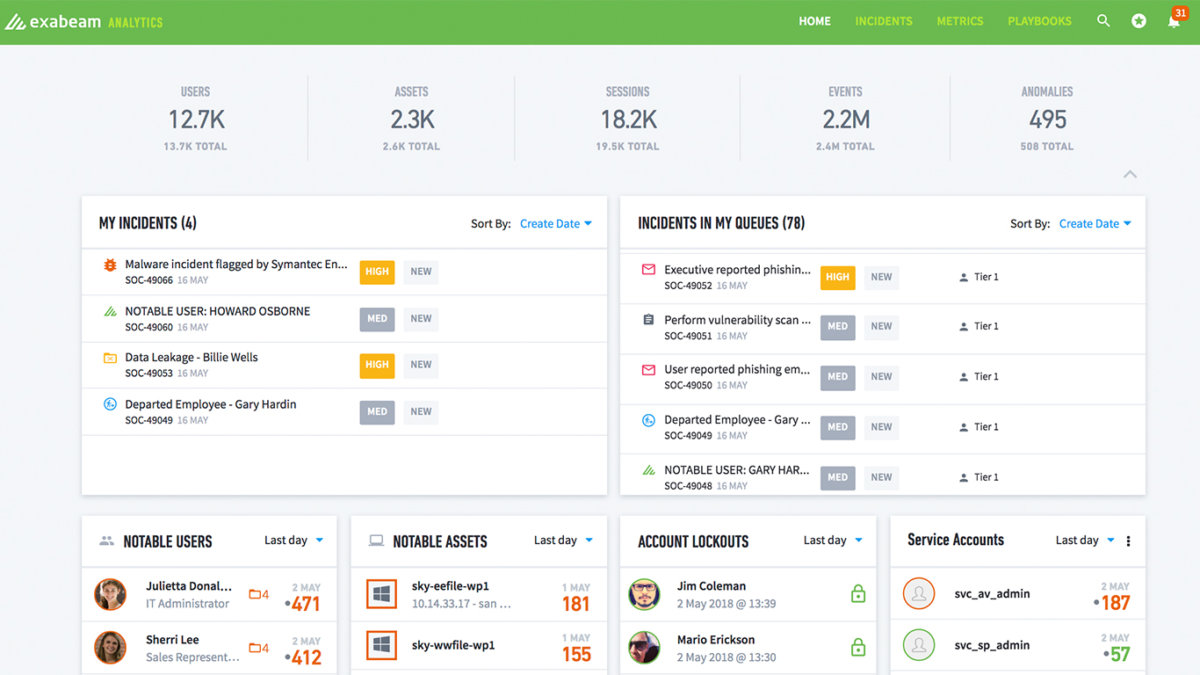
How SIEM works with the SOC
Security Operation Center (SOC)
The task of a SIEM is to provide the Security Operation Center (SOC) with detailed insights from the analysis of event data. This data is so extensive that it would otherwise not be used for manual analysis. In order to detect threatening activities in time, the SIEM analysis of machine data log files is used to uncover and thus gain valuable response time.
A Security Operation Center (SOC) works together with a SIEM to specifically defend against internal or external attacks. The goal is always to continuously simplify threat management, minimize potential risks and ensure company-wide transparency. The comprehensive overview of a Security Intelligence (SI) is in the foreground.